You see the headlines every week: A major hospital network, a city government, or a Fortune 500 company has been crippled by a cyberattack. The hackers are demanding millions of dollars, or they will leak the company’s most sensitive data to the public.
But where does this “leaking” actually happen?
It happens on the Dark Web. Modern ransomware gangs operate like twisted corporations. They don’t just lock computers; they steal the data first and post it on their own PR websites-known as Dedicated Leak Sites (DLS)-to publicly shame the victims into paying.
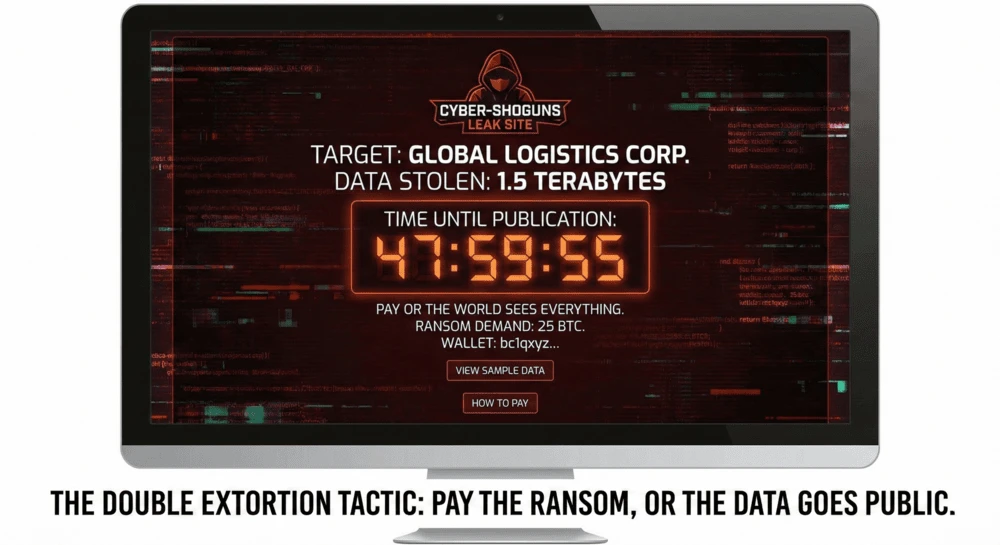
Here is how Open Source Intelligence (OSINT) analysts and Threat Intelligence researchers track these cybercriminal cartels in real-time.
What is a Dedicated Leak Site (DLS)?
In the old days of ransomware, hackers would just encrypt a computer and leave a ransom note on the desktop. If the company had good backups, they would just restore their systems and ignore the hackers.
To counter this, ransomware groups invented “Double Extortion.” Now, they steal terabytes of employee passwords, financial records, and customer data before locking the computers.
They then post the victim’s name on a .onion website on the Tor network. They start a countdown timer. If the timer hits zero and the ransom isn’t paid, the data is published for the whole world (and rival scammers) to download.
Method 1: The OSINT Aggregators (The Safe Way)
If you are an independent researcher or just curious about who got hacked today, you should never visit a ransomware gang’s actual Dark Web site. These sites are frequently booby-trapped with malware that tries to infect the computers of the researchers watching them.
Instead, use surface-web OSINT aggregators. These are legitimate cybersecurity companies that monitor the Dark Web 24/7 and publish the data safely on the clear web.
The Best Tools:
- Ransomwatch: An open-source project that scrapes the leak sites of dozens of ransomware groups (like LockBit, ALPHV, and Play) and provides a daily feed of their newest victims.
- FalconFeeds.io: A free threat intelligence dashboard that tracks ransomware claims, Dark Web forum chatter, and data breaches in real-time.
How to use them: If a local business in your town suddenly closes “due to a network outage,” you can search these aggregators. If you see the company’s name listed, you instantly know it wasn’t a glitch-it was a ransomware attack.
Method 2: Analyzing the Extortion Tactics
When threat researchers look at a ransomware leak site, they aren’t just looking at the victim’s name. They are gathering OSINT on the attacker’s tactics.
What researchers look for:
- The “Proof” Documents: Gangs will often publish 2 or 3 highly sensitive documents (like a CEO’s passport or a corporate bank statement) as “proof of life.” Analysts review these to verify the hack is real.
- The Affiliate Network: Many ransomware groups operate as “Ransomware-as-a-Service” (RaaS). The developers rent their malware to freelance hackers (affiliates). By analyzing the language and targets on the leak site, researchers can profile the specific affiliate who carried out the attack.
- The Infrastructure: Advanced OSINT investigators use tools to scan the underlying servers hosting the
.onionsite, looking for operational security (OPSEC) mistakes that might reveal the gang’s real-world physical location.
Method 3: Following the Cryptocurrency
Ransomware gangs don’t take credit cards. They demand payment in Bitcoin or Monero.
Often, the ransomware gang will post their cryptocurrency wallet address directly on the leak site so the victim knows where to send the millions of dollars.
The OSINT Takedown: The moment a wallet address is posted publicly, blockchain investigators go to work. Because the Bitcoin ledger is public, researchers can trace exactly where the ransom money goes.
They watch the gang try to “tumble” or “mix” the coins to hide them, and they alert federal authorities the second the hackers try to cash out the crypto at a real-world bank.
Summary: The Threat Intel Protocol
| Tool/Tactic | What It Does | Safe for Beginners? |
|---|---|---|
| Ransomwatch / FalconFeeds | Surface-web aggregators tracking ransomware victims. | Yes (Highly Recommended) |
| Blockchain Analysis | Tracing the public extortion payments. | Yes (Requires technical skill) |
| Direct .onion Monitoring | Visiting the actual hacker leak sites. | No (High risk of malware) |
The Bottom Line
The Dark Web isn’t just a place for buying illegal goods; it is the boardroom for modern cyber warfare.
By understanding how ransomware gangs use Dedicated Leak Sites to extort their victims, you can see past the media headlines and understand the actual mechanics of a cyberattack.
Next Step: Are you worried your company might be the next target? Start defending your perimeter today. Use our Shodan OSINT Guide to check if your corporate servers or remote-work portals are accidentally exposed to the public internet.

