It usually starts innocently. You look at your phone and see a text message from an unknown number:
“Hi David, are we still meeting for golf at 3 PM?”
Or perhaps:
“Is this the pet groomer? My dog needs an appointment.”
You know you aren’t David, and you certainly aren’t a pet groomer. Your instinct is to be polite, so you reply: “Sorry, wrong number.”
Normally, that would be the end of it. But in this scenario, the stranger replies immediately:
“Oh, I am so sorry! I must have saved the number wrong. You seem like a very nice person for replying, though. My name is Anna, I’m from Singapore but living in LA now. Let’s be friends!”
Stop right there.
This is not a mistake. It is not fate. This is the opening move of a sophisticated, multi-billion dollar cybercrime operation known as “Pig Butchering” (or Sha Zhu Pan).
According to the FBI’s 2023 Internet Crime Report, investment fraud scams like this resulted in over $4.5 billion in losses in a single year.
Here is the intelligence you need to spot the scam, understand the endgame, and protect yourself.
The Script: Recognizing the Lure
Scammers use automated software to send thousands of these texts per day. They are “phishing” for active numbers-people who are willing to reply.
While the stories change, the templates (scripts) remain the same. Look out for these three common variations:
-
The Appointment Mix-Up
- The Text: “Hi, is this [Name]? I’ve arrived at the meeting place.”
- The Goal: To create a sense of urgency so you reply quickly without thinking.
-
The Business Inquiry
- The Text: “Manager Wang, have you reviewed the financial reports for the quarter?”
- The Goal: To sound professional and wealthy, setting the stage for an investment scam later.
-
The “Assistant” Mistake
- The Text: “Hello, I am the assistant to Mr. Li. Is this the flower shop?”
- The Goal: To establish a hierarchy where the scammer poses as a wealthy elite or their associate.
The “Why”: What is the Pig Butchering Scam?
Why do they go through all this trouble just to say hello?
In the cybersecurity world, this specific threat is called Sha Zhu Pan (Chinese for “Pig Butchering”). The analogy is dark but accurate:
- The Fattening: The scammer spends weeks or months building a relationship with the victim (the “pig”). They build intense trust, friendship, or even romance.
- The Butchering: Once trust is established, they introduce a “foolproof” cryptocurrency investment opportunity. Once the victim invests their life savings, the scammer disappears.
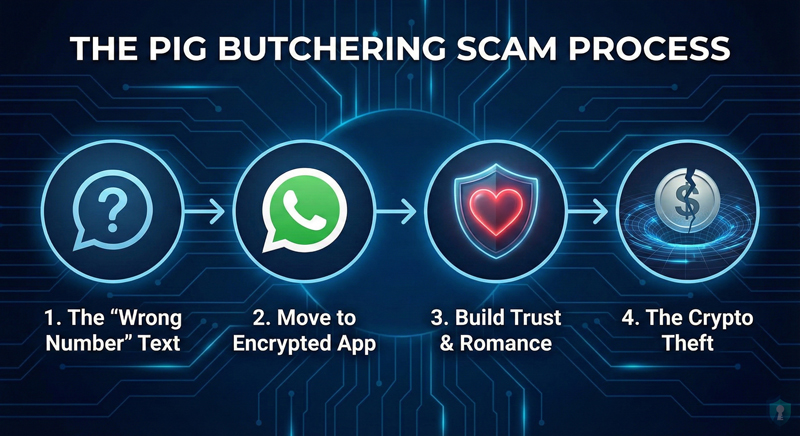
The 4 Phases of the Attack
- Contact: The “wrong number” text breaks the ice.
- Migration: They immediately try to move you to an encrypted app like WhatsApp or Telegram.
- The Lifestyle: They send photos of luxury cars, expensive food, and charts showing massive crypto profits.
- The Kill: They convince you to put a small amount of money into a fake trading platform. It works at first (they let you withdraw a little profit), but then they drain your account.
Red Flags: How to Spot It Immediately
You don’t need to be a cybersecurity expert to spot these. You just need to look for these behavioral red flags:
- The “Polite” Persistence: A normal person who texts a wrong number says “Sorry” and stops texting. A scammer will try to keep the conversation going by asking about your location, your job, or your age.
- The “Fate” Narrative: They will often say things like, “Fate must have brought us together” or “It is destiny that I texted you.”
- The WhatsApp Push: This is the biggest warning sign. If a stranger texts you via SMS and immediately says “My signal is bad, add me on WhatsApp,” block them immediately. They do this to hide from your phone carrier’s spam filters.
- The Profile: Scammers often use stolen photos of attractive young women (or handsome men) to lower your defenses.
Actionable Intel: What To Do
If you receive one of these texts, follow these three rules of engagement:
Rule #1: Do NOT Reply
This is critical. Even typing “Stop” or “Wrong number” gives the scammer valuable data. It tells them:
- This phone number is active.
- A real human monitors this phone.
If you reply, your number will be added to a “Sucker List” and sold to other scammers. You will start receiving more spam calls and texts.
Rule #2: Do NOT Troll Them
It might be tempting to waste their time or make jokes (“scambaiting”). However, these operations are often run by organized crime syndicates. If you antagonize them, they may mark your number for harassment, signing you up for thousands of spam calls.
Rule #3: Report and Block
Don’t just delete the text-report it so the network can stop it.
- In the US, UK, and Canada: Forward the scam text message to 7726 (spells “SPAM” on the keypad). This alerts your mobile carrier (AT&T, Verizon, T-Mobile, etc.) to investigate the number.
- On iPhone: Swipe left on the message and tap Report Junk.
- On Android: Long press the message and select Block & Report Spam.
Frequently Asked Questions
Q: Can they hack my phone just by texting me?
A: Generally, no. Receiving a text does not hack your phone. However, never click links inside these text messages. Clicking a link can install malware or take you to a phishing site.
Q: Why are most of the texts from “Asian women”?
A: This specific scam (Sha Zhu Pan) originated in Southeast Asia. The scammers use stolen photos of attractive influencers to appeal to loneliness and build trust quickly.
Q: I accidentally replied. What should I do?
A: Don’t panic. Just stop responding immediately. Do not answer their calls. Block the number. You may see an increase in spam for a few weeks, but if you stay silent, they will eventually move on to an easier target. If you have already lost money, we recommend contacting dedicated victim support groups for assistance.
The Bottom Line
In the digital age, skepticism is your best defense. No legitimate friendship or investment opportunity starts with a “wrong number” text message.

